中国运营商海陆光缆的布局、挑战与破局
https://www.eet-china.com/mp/a204489.html
海底光缆(下称“海缆”)和陆地光缆(下称“陆缆”),是当今全球网络通信的重要基础设施。
它们不仅代表一个国家的通信发展水平,还影响着科教能力、经济发展和民生福祉,甚至安全层面 。
既然海陆缆于一国而言具有如此重要的意义,那么,中国运营商在海外有哪些布局?当前面临着什么挑战?如何破局?
█ 海陆缆简介
关于海陆缆的特点,笔者之前在《海缆通信 VS 陆缆通信》一文中作过详细介绍,总结起来,有以下四个方面。
● 带宽容量:一般而言,海缆的容量比陆缆更大。
● 网络时延:海缆与陆缆的时延各有千秋,取决于具体的物理路由。
● 运行稳定性:海缆要么正常,要么中断,修复起来慢;陆缆中断的情况较少,但抖动(倒换)可能较多。
● 市场价格:对于中长距离的国际传输,一般情况下陆缆的价格要高于海缆。
█ 我国海陆缆的特点
我国国际海陆缆发展的特点是:起步较晚,发展较快,瓶颈较多。
1、起步较晚
世界上第一条光缆,是 1988 年美国与英国、法国之间铺设的大西洋海底光缆(TAT-8),全长 6700 公里。
这条光缆含有 3 对光纤,每对的传输速率为 280 Mbps,中继站距离为 67 公里。大西洋海底光缆的建成,标志着海底光缆时代的到来。
我国直至 1993 年底,才开通第一条海底光缆——中日海底光缆。 中日海底光缆从上海南汇至日本九州宫崎,全长 1252 公里,通信总容量达 7560 条通话电路。中日海底光缆的开通,使得当时中国国际通信能力增长 80% 以上,标志着中国从此向互联网进军。
中日海底光缆成功登陆,引用自互联网公开信息
2、发展较快
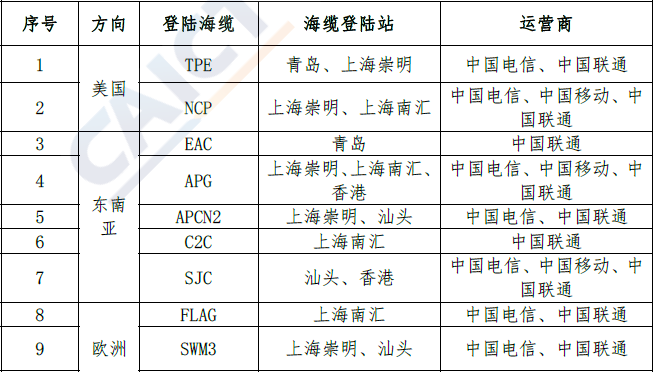
在国际海缆方面,根据中国信通院发布的信息,经过多年的建设,目前在中国大陆登陆的国际海缆共有 9 条,中国运营商在登陆海缆上现有带宽超过 40 Tbps 的带宽,并且这一数字还在不断增长,具体如下。
在中国大陆登陆的海缆(引用自中国信通院发布的《中国国际光缆互联互通白皮书》)
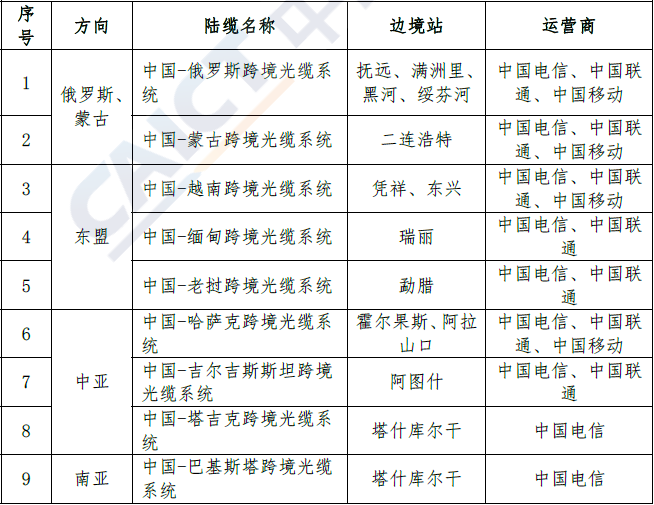
在跨境陆缆方面,中国更是取得了长足的进步。通过跨境陆缆,中国已经建成了连接周边国家、通达欧洲的陆地光缆网络架构,系统带宽超过 70 Tbps,具体如下。
中国跨境陆缆统计表(引用自中国信通院发布的《中国国际光缆互联互通白皮书》)
3、瓶颈较多
然而,尽管近年来中国运营商在国际海陆缆建设方面发展较快,但相比一些发达国家,仍然存在较大差距和诸多不足,具体有以下几个方面。
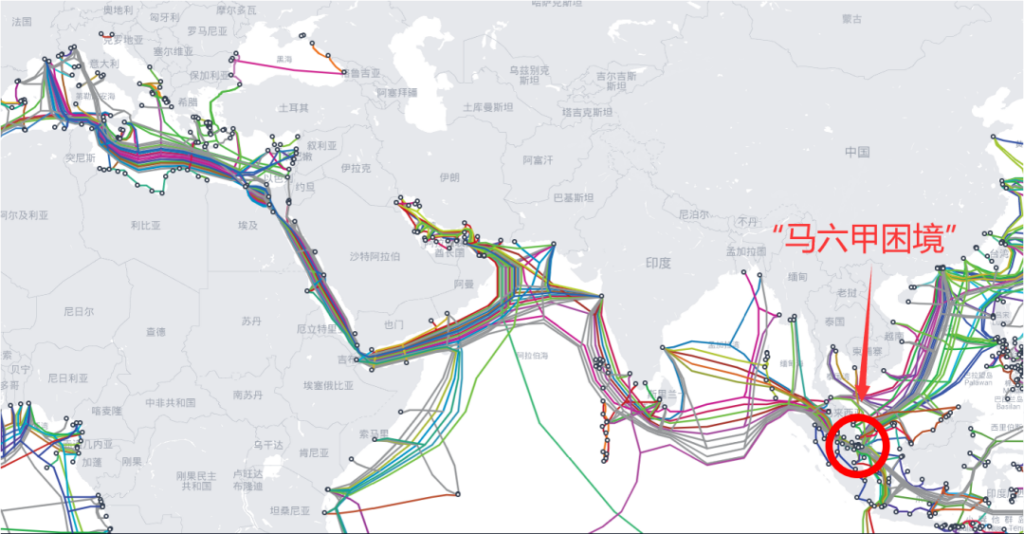
● “马六甲困境”
目前几乎所有从中国去往中东、欧洲或非洲地区的海缆,均需要途经马六甲海峡,由于某些因素,万一马六甲海峡局势有变化,这必然会影响中国与世界的通信,进而波及中国“一带一路”发展战略的推进。
图:中国海缆通信的“马六甲困境”
● 美国无法上岸
目前,中国运营商投资建设了一些在美国登陆的海缆,并拥有一定的带宽权益,例如 TPE、FASTER 和 NCP 等。而随着中国电信、中国联通的 “214 牌照”于 2021 年和 2022 年相继被美国吊销,导致中国运营商的海缆资源将无法在美国上岸,而面临被动局面。
注:“214 牌照”,是指根据美国通信法(1934 年版及 1996 年修订版)第 214 条规定,取得的 FCC 颁发的国际电信业务授权——在美国与外国之间提供国际公共运营商通信服务。
● 非洲存量为零
非洲作为中国“一带一路”战略的重要区域,聚集了大量的中资企业。这些企业背靠强大的祖国,在非洲投资、建设与生产,不少已经扎根非洲。然而,非洲相对落后的通信基础设施,将日益成为中资企业进一步发展的瓶颈。
据了解,当前非洲国家之间主要依靠海缆进行通信(陆缆资源发展落后),而可选的只有 SAT-3/WASC、EASSy 和 ACE 等寥寥数条由欧洲运营商主导建设的海缆,且价格昂贵。这客观上制约了中国运营商在当地的网络服务能力。
█ 未来动向
可喜的是,面对上述发展的困境,中国运营商背靠强大的祖国,在海陆缆发展方面进行了前瞻性的战略布局,并取得了重要积极的进展。
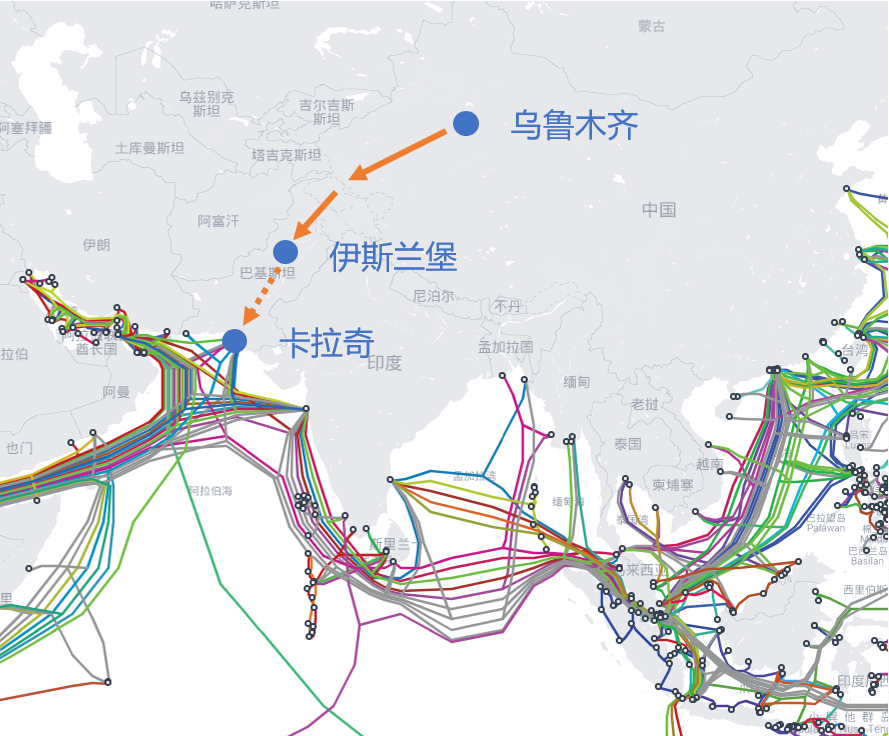
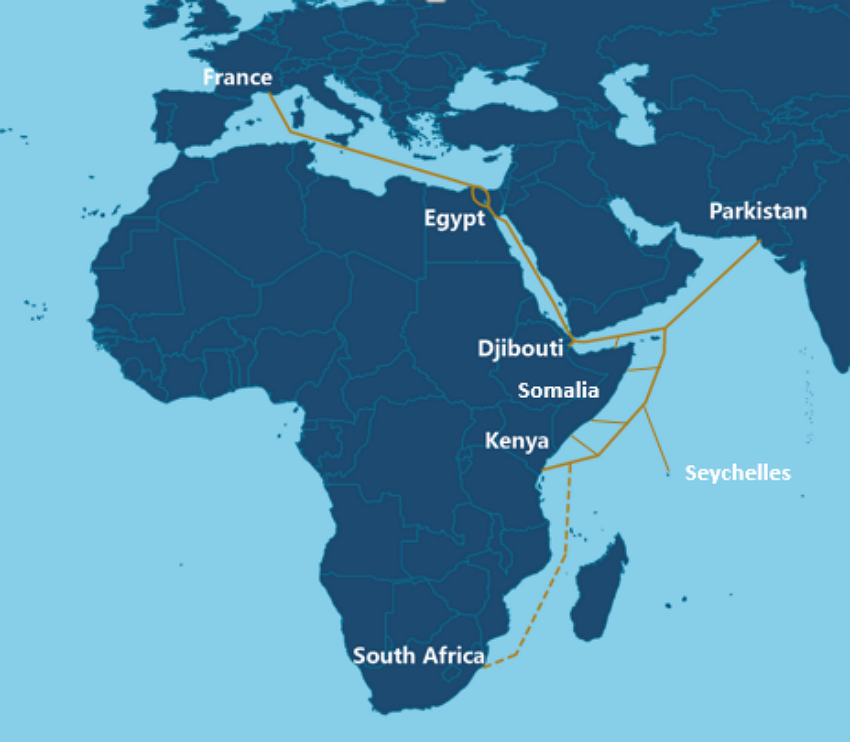
1.打通中巴陆缆——冲破“马六甲困境”
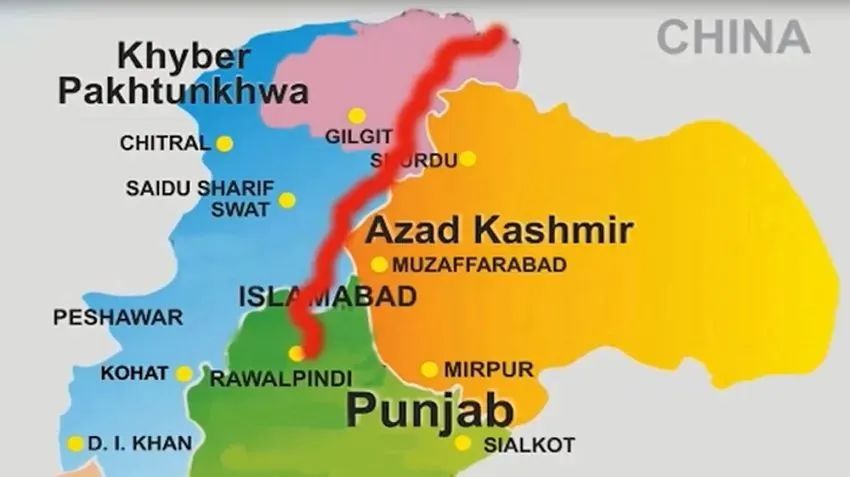
首先是中国电信于 2018 年率先开通中国-巴基斯坦首条跨境陆地光缆系统(下称“中巴光缆系统”),这标志着中巴两国通信网络基础设施互联互通建设取得重大进展。
中巴光缆系统,引用自《中国电信建成开通中国-巴基斯坦首条跨境陆地光缆》
中巴光缆系统只是一个开始,随着中巴两国战略合作的进一步深入,相信在不久的将来,中巴光缆将有望从伊斯兰堡延伸至港口城市卡拉奇,并与卡拉奇海缆对接。如此一来,海缆通信的“马六甲困境”将迎刃而解,对中国的战略意义不言而喻。
中巴光缆系统(图中橙色实线),及其延伸段(图中橙色虚线)
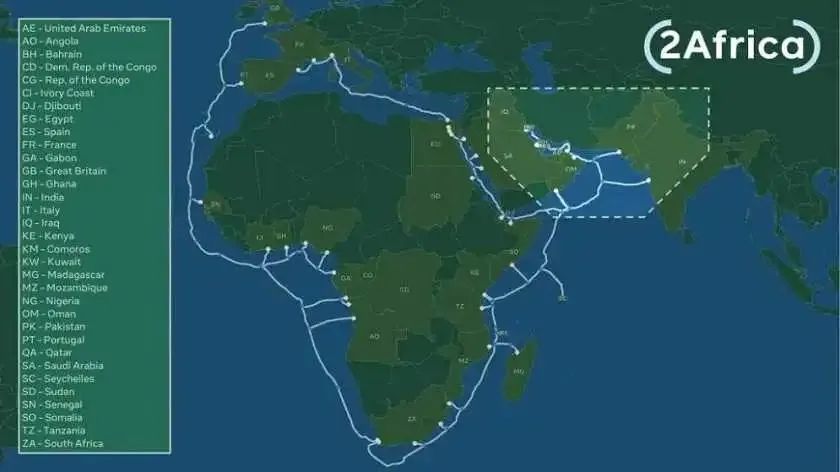
2.投资建设 2Africa 海缆——强化非洲网络覆盖能力
非洲人口众多,市场广阔,发展潜力巨大,是中国“一带一路”发展战略的重要阵地,然而,通信基础设施落后也是许多非洲国家在经济发展中绕不开的问题。
为了更好地助力中资企业出海,增强中国在非洲乃至全球的影响力,中国移动于 2020 年,投资建设 2Africa 海缆系统。
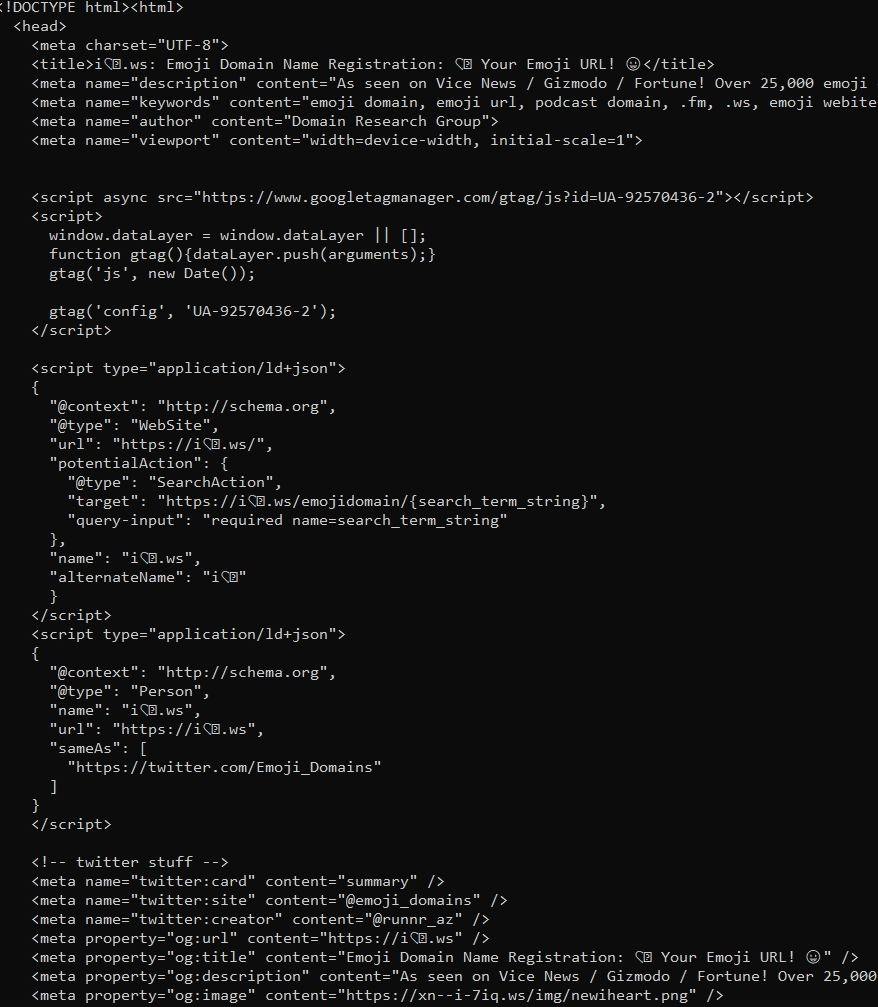
2Africa 海缆(含中东 PEARLS 分支)全长45000 公里,预计于 2023 年末建成投产,届时将是世界上人最长的海底光缆系统,覆盖超过全球超过三分之一的人口。
2Africa 海缆,引用自《2Africa to become world’s longest subsea cable post Arabian, Asian expansion》
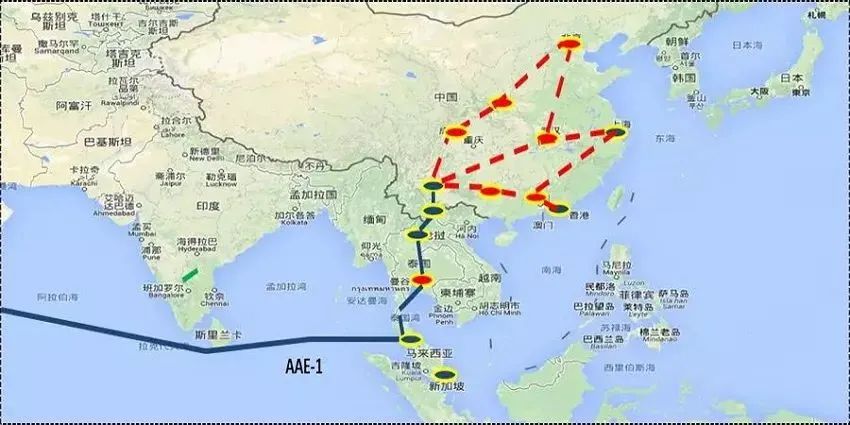
3.积极拓展中越、中泰、中缅和中老等方向的对接
中国人西南邻国众多,与中国的经济、政治和文化联系紧密。在“睦邻友好、和平发展”方针下,近年来中国运营商正积极与越南、泰国、缅甸和老挝等国进行陆网方面的合作。
根据公开资料显示,目前中国电信已建成中老泰陆缆系统,中国移动也已打通中越、中泰等方向的陆缆通信信道。
向西南方向的陆缆拓展,一方面加强了中国与东南亚国家的联系,另一方面也是为信息出海方向提供更多的选择性。
中国电信中老泰陆缆,引用自《中国电信成功开通中老泰陆缆》
信息化是智能制造的前提,而海陆缆则是信息化的重要基础设施。伴随着中国“一带一路”发展战略的推进,接下来我们将在全球海陆缆建设中看到更多的中国身影和中国元素。
https://www.submarinenetworks.com/zh/zx/hll/20220512
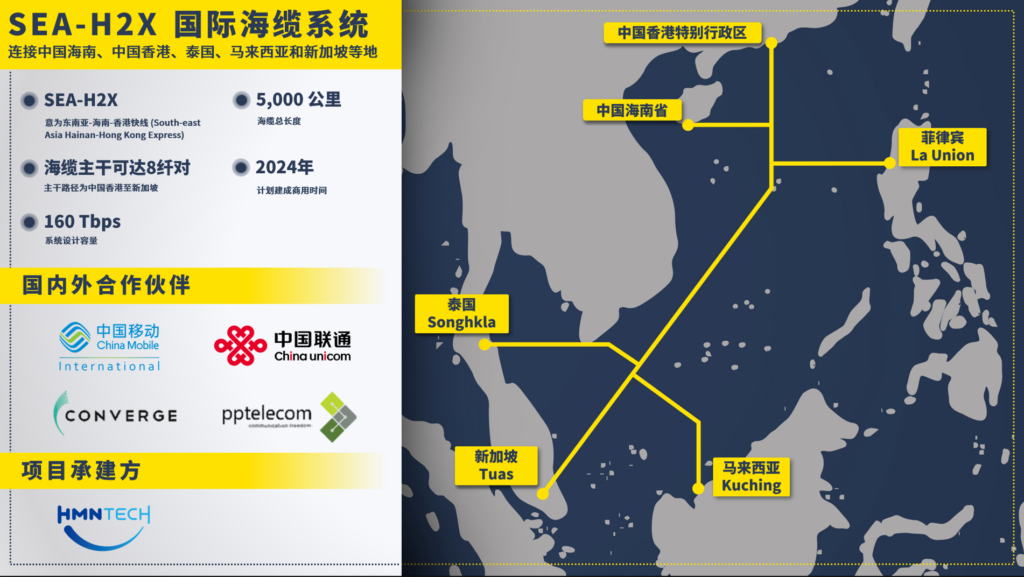
中国移动国际、中国联通国际等携手华海通信 共同宣布建设SEA-H2X国际海缆 使能亚洲互联新时代
2022年5月12日,【天津,中国】—— 中国移动国际有限公司(CMI)、中国联通国际有限公司(CUG)、Converge Information and Communications Technology Solutions, Inc.(Converge)以及PPTEL SEA H2X Sdn. Bhd(PPTEL SEA H2X)近日宣布计划合作铺设SEA-H2X国际海缆系统,为亚洲及全球数字化转型扩容提速。SEA-H2X将连接中国海南、中国香港、菲律宾、泰国、马来西亚及新加坡等地,进一步可延伸至越南、柬埔寨以及印度尼西亚,建成后将极大提升亚洲区域内的网络连接性。SEA-H2X由国际海缆联盟成员共同运营,由华海通信技术有限公司(HMN Tech)承建。
SEA-H2X国际海缆全长将超过5,000公里,采用高规格光纤布线,其设计容量高达160 Tbps,新加坡和中国香港两地间线路将采用至少8对光纤部署。SEA-H2X海缆计划于2024年投入使用,届时将有效满足亚洲地区对网络带宽和高速连接日益增长的需求,助力共建5G演进的网络新生态,为全球数字经济蓬勃发展提供更大助推力。
SEA-H2X海缆系统由华海通信提供海缆系统的端到端解决方案,包含海缆系统及水上水下设备的设计、生产、建设和施工。该系统应用了先进的 Open Cable技术,使其可灵活地选择最优的海底线路终端设备(SLTE),达到传输能力最大化。此外,该项目还应用了全球领先的海底线路分支器(BU)和海底线路动态光分插复用器(ROADM)将为SEA-H2X海缆系统提供超高的可靠性和光电线路的高灵活性。
路由图:
https://www.submarinenetworks.com/zh/zx/hll/peace-20180829
https://www.submarinenetworks.com/zh/zx/hll/20211020
https://www.submarinenetworks.com/zh/zx/hll/2018102201
PEACE国际海缆网络系统有限公司(亨通集团子公司)和华为海洋网络有限公司今日联合宣布,PEACE海缆项目进入海缆和设备生产环节。该海缆项目全程12,000公里,将连接亚洲、非洲和欧洲,并计划在2020年第一季度提供商用服务。
https://www.submarinenetworks.com/en/stations/asia/china
China
现在有以下海底电缆登陆中国大陆:
通往美国的电缆:
China-US CN (retired)
TPE
NCP
连接亚洲的电缆:
APCN-2
APG
EAC-C2C
SJC
SJC2 (2021)
TSE-1
Xiamen-Jinmen
Hainan to Hong Kong Express (H2HE )
通往非洲和欧洲的电缆:
这些电缆降落在中国的 9 个海底电缆登陆站。
中国电信拥有三个光缆登陆站,包括
中国联通拥有四个电缆登陆站,包括:
中国移动拥有两个电缆登陆站:
Lingang Cable Landing Station for NCP and SJC2;
Wenchang Cable Landing Station for Hainan to Hong Kong Express (H2HE )